Water treatment, pipelines, and email…. Oh my!
Key Takeaways
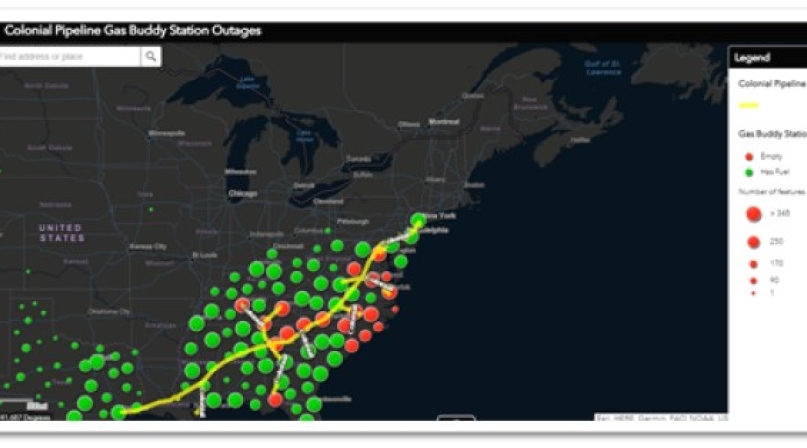
What do water treatment, pipelines and email all have in common? In the past few months, each has been attacked either by ransomware or a malicious virus. The cyberattack on the water supply in Florida occurred in early February. Shortly thereafter the Microsoft exploit attacked email systems across the world. And now in the past week, we all have heard and in some cases been directly affected by the cyberattack on the Colonial Pipeline. This pipeline stretches from Texas to New York and on May 7, Colonial Pipelines’ business systems became the victim of a ransomware attack. This type of attack denied the company access to its IT systems and data. The group identified as Darkside held the company hostage until a ransom was paid. While the safety of the pipeline was not compromised, the company made the decision to proactively disconnect certain systems that monitor and control physical pipeline functions so that they would not be compromised. This resulted in a temporary halt to all pipeline operations. On May 13, Colonial Pipeline restarted the pipeline and product delivery.
Overall 49 percent of gas stations in Virginia and 45 percent in both Georgia and South Carolina went dry temporarily. The governor of North Carolina even declared a state of emergency.
Learn More
These NACo resources, along with the Cybersecurity and Infrastructure Security Agency resources, provide valuable options for counties to improve their cybersecurity defenses. Please share these resources with your information technology leaders and support.
- Joint Ransomware Guide (CISA and Multi-State Information Sharing and Analysis Center)
- CISA Ransomware Webpage: Ransomware Guidance and Resources
- CISA Insights: Ransomware Outbreak
- CISA Pipeline Cybersecurity Initiative
- CISA Pipeline Cybersecurity Resources Library
Taking a proactive stance, the Department of Homeland Security, along with the FBI and the White House National Security Council, hosted national calls providing updates for public and private entities. NACo and county IT Leaders were able to participate in these calls and receive great guidance and reaffirmation of the cyber basics that every county should be paying attention to. Below are those best practices:
- Multi-Factor Authentication (MFA) should be on IT and operational accounts.
- Manage phishing emails, including strong email filtering and end user trainings.
- Address or at least identify out of date/end of life unpatched software.
- Limit access to resources over the network by ensuring default settings or “ports” are shut down if not needed.
- Monitor/block inbound connections from various services.
More details and other best practices are included in CISA’s alert.. Counties were also reminded of several other positions they should be taking to mitigate such attacks. These mitigation strategies included segmenting your operational technologies from the business application technologies, identifying your most critical data ensuring that it is encrypted and validating that there are offline backups of that critical data.
In the end, Colonial Pipeline paid the ransom with bitcoin that amounted to nearly 5 million dollars! We are not going to debate the merits of whether to pay the ransom or not. Depending on who you talk to there are distinct opinions and recommendations around paying the ransom. White House press secretary Jen Pskai emphasized on May 13 that in general the US government encourages victims not to pay, but others in the administration struck a more measured position. Making that decision to pay the ransom is a balancing act for sure!
It is important to remember that this is not the end of ransomware attacks. Therefore, counites need to be focused on reinforcing and growing their cyber defenses. In addition to the MS-ISAC resources shared below, NACo is offering quarterly cyberattack simulations for counties to spend a week (one hour each day) participating in a tabletop exercise and daily injections of information. To learn more, you can go to: https://www.naco.org/naco-cyberattack-simulation. The next simulation is set for June 21-25.

Attachments
Related News

National Association of Counties Launches Initiative to Strengthen County Human Services Systems
The National Association of Counties (NACo) announces the launch of the Transforming Human Services Initiative, a new effort to help counties modernize benefits administration, integrate service delivery systems and strengthen county capacity to fulfill our responsibility as America’s safety net for children and families.


