Focus on employees during National Cybersecurity Awareness Month
Author

Dr. Alan Shark
Upcoming Events
Related News

Key Takeaways
National Cybersecurity Awareness Month (NCSAM) — celebrated every October — was created as a collaborative effort between government and industry to ensure that every American has the resources they need to stay safer and more secure online.
NACo along with the Public Technology Institute (PTI) are members and sponsors of the Multi-State Information Sharing and Analysis Center (MS-ISAC), a nonprofit funded by the U.S. Department of Homeland Security (DHS). MS-ISAC and it’s newest sibling Elections Infrastructure — ISAC — provide a host of free services to counties that are aimed at protecting local government infrastructure.
While we can rest assured (at least many of us can) that trained professionals are at work 24/7 protecting our county’s digital infrastructure, the message for this campaign is all about increasing county employee awareness as cybersecurity is clearly an all-hands effort.
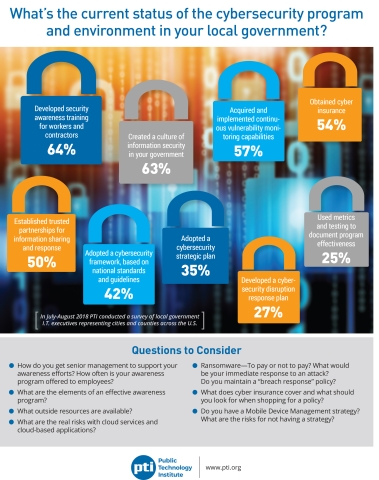
PTI’s latest survey reveals that 64 percent of local governments provide cybersecurity awareness training for workers and contractors with 63 percent claiming to have created an information security culture. While this is an improvement over previous years much more needs to be done at a time when cyberattacks are very much on the rise.
Personal responsibility is of upmost importance when it comes to protecting a county’s infrastructure. The “bad guys” are always looking for weaknesses and vulnerabilities. Here are seven simple things a county can do and should be a core component in any cyber-awareness plan:
1. Passwords still matter. Using different passwords that contain and include at least eight characters with numbers and symbols. Try and come with a formula where you can remember them too. For example, you may use and old address as a starter or transpose a letter for a number or symbol. Passwords should not begin with a capital letter, and underscore is a good way to separate a bunch of numbers.
2. Use multiple passwords. By using multiple passwords for different accounts, you spread the risk of having one breach expose you to everywhere you have a login account. Too many passwords to remember? Consider using a “password manager” like LastPass or Dashlane. Most offer free versions that one can try out. While these systems require a complex master password, password managers do the rest. You can elect to have them assign complex random passwords and most have an autofill feature that fills in the necessary fields automatically. Another advantage is most password managers remember and recall passwords and payment information across your devices if you so choose. This includes PC, laptops, and all your mobile devices.
3. Think before you click. Ransomware and phishing attacks have increased dramatically the past two years. Many of these attacks can be traced to employees clicking and opening attachments. Before you open an attachment are you sure it is from a person or entity they say they are? Do you see suspicious signs like misspellings, using a salutation such as “dear customer” instead of your name, a return URL or address that is different from the senders? For example, if you receive something that appears to be from your bank, is the URL taking you to the bank or is it directing you somewhere else. It’s always best not to click on such emails regardless of how real they look. Instead simply go directly to the company’s site and see if there is any real issue for you to resolve. Finally, if in doubt always contact your IT folks as they have ways of checking authenticity without risk to others.
4. Limit address book entries. It is shocking to learn how many professionals use their mobile device address books to store credit card numbers, passwords, family social security numbers and birthdates. As tempting as it is, don’t use your mobile device’s directory as your personal information database. Most cyber breaches attack your address books and yes, these same rogue software programs are programmed to search for this type of information in addition to all your contacts. Remember, the bad-guys goal is to exploit ever bit of information they can and use it to cause further havoc which could lead to identity theft, use passwords to enter systems to obtain further a perhaps more important information.
5. Update your devices. Computer and mobile device manufacturers are routinely updating their operating systems to help improve performance as well as actively addressing known security vulnerabilities. It should go without saying, make sure you not only have the best virus and malware protection, but also system updates in real-time to gain maximum protection.
6. Avoid public Wi-Fi. It is always tempting for on-the-go-people to connect every time they see a Wi-Fi hotspot. There are plentiful offerings at airports, trains, coffee shops, hotels, and conferences. Unfortunately, public Wi-Fi (free or not) can easily be exploited by the bad-guys who can “see” what you are logging into with not much effort and be able grab your passwords. Never conduct business in public places offering Wi-Fi that requires passwords, which might include logging into your office or your bank. Consider having your own mobile hotspot offered by all wireless carriers. Even though you are still connecting via Wi-Fi it is far more difficult to snoop and the data is usually encrypted and ultimately converted to more secure cellphone frequencies.
7. Report suspicious attachments and electronic messages. Unlike “yesterday’s” policies, county staff should be encouraged to quickly come forward when something doesn’t look right or they clicked on something they realized a moment later they should not have. Early reporting is far better than any shortsighted punishment. Some policies in the past were punitive and actually discouraged early reporting; today, this needs to be reversed. Encourage and reward for early reporting and state penalties for failure to report in a timely manner.